This is the ninth installment in our series on microservices architecture patterns. In previous posts, we've explored topics such as synchronous and asynchronous communication, process orchestration, and fault tolerance. If you're looking for a comprehensive overview of how to design, deploy, and operate microservices professionally, we recommend reviewing the earlier posts:
- Microservices Architecture Patterns: What Are They and What Benefits Do They Offer?
- Architecture Patterns: Organization and Structure of Microservices.
- Architecture Patterns: Microservices Communication and Coordination.
- Microservices Architecture Patterns: SAGA, API Gateway, and Service Discovery.
- Microservices Architecture Patterns: Event Sourcing and Event-Driven Architecture (EDA).
- Microservices Architecture Patterns: Communication and Coordination with CQRS, BFF, and Outbox.
- Microservices Patterns: Scalability and Resource Management with Auto Scaling.
- Architecture Patterns: From Monolith to Microservices
In today’s modern IT landscape, microservices have become one of the preferred strategies for designing and scaling complex applications.
This article focuses on a key architectural pattern: Externalized Configuration, and we’ll explore:
- How to isolate and protect sensitive information, avoiding hardcoding credentials in your codebase.
- Methods to externalize and manage configuration (environment variables, external files, configuration servers).
- Detailed examples based on an eCommerce system using Spring Boot, Docker, and Kubernetes.
The eCommerce context is ideal to illustrate this pattern, just like in the rest of our series, since it involves multiple domains and specialized services: a product catalog, order module, payment service, logistics service, and more. Each of these has its own dependencies, configurations, and exposed APIs consumed by other modules.
Challenges of Configuration Management in a Microservices Environment
Before diving in, let’s reinforce why this pattern is essential in microservices architecture:
- With many microservices, each one may require endpoints for other services, database credentials, feature flags, or performance parameters.
- Hardcoding this configuration into the service’s codebase poses security risks (e.g., exposing secrets) and maintainability challenges (changes require redeployments).
- Working across multiple environments (dev, test, staging, production) further multiplies configuration complexity.
With this context in mind, let’s break down the pattern and how to implement it—with a strong technical focus.
Externalized Configuration
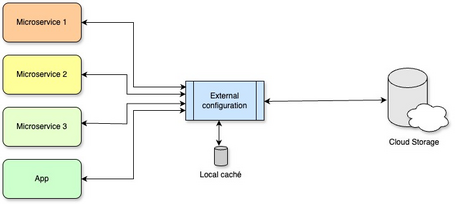
*Storage doesn’t need to be cloud-based.
1 Pattern Fundamentals
Externalized configuration is based on the principle that all variable or sensitive service information should live outside the binary itself. That means credentials, payment gateway tokens, dependency URLs, or business parameters should not be embedded in the source code or internal config files—they should be injected at deploy time, or ideally, managed by a separate service.
2 Key Benefits
- Security and Governance
- Reduces the chance of secrets or API keys being committed to public repos or build logs.
- Easier to apply access controls and audit changes.
- Deployment Flexibility
- A single Docker image (or JAR package) can move through the pipeline from dev → test → staging → prod, with the appropriate configuration injected at each step.
- Parameters can be changed without recompiling, saving time and reducing errors.
- Maintainability and Scalability
- With dozens or hundreds of microservices, a shared configuration repository (or config service) simplifies orchestrating and updating shared values (like a common service URL).
3 Methods to Externalize Configuration
Broadly speaking, there are three common approaches: environment variables, external files, and centralized configuration services. Let’s examine each in more detail.
- Environment Variables
- In containerized environments (Docker, Kubernetes), this is the most basic and 12-Factor App–aligned method.
- Each microservice retrieves its values at runtime.
- Easy to manage with orchestrators (Kubernetes ConfigMaps and Secrets), though scalability may become an issue with many properties.
Docker: When launching a container with docker run, we can define:
docker run -d \
-e DB_USER=admin \
-e DB_PASS=secret123 \
-e SPRING_PROFILES_ACTIVE=prod \
--name orders-service \
myrepo/orders-service:latest
Here, DB_USER and DB_PASS are read within the service using System.getenv(), or via properties in Spring Boot (spring.datasource.username=${DB_USER}, etc.)
Kubernetes: a ConfigMap is used for generic variables and a Secret is used for credentials or sensitive values.
Here’s an example of a Deployment:
apiVersion: apps/v1
kind: Deployment
metadata:
name: orders-service
spec:
replicas: 2
selector:
matchLabels:
app: orders-service
template:
metadata:
labels:
app: orders-service
spec:
containers:
- name: orders-service
image: myrepo/orders-service:latest
env:
- name: DB_USER
valueFrom:
configMapKeyRef:
name: orders-config
key: db-user
- name: DB_PASS
valueFrom:
secretKeyRef:
name: orders-secrets
key: db-pass
This way, each pod inherits the appropriate configuration.
Advantages:
- Simple to use and manage in containerized environments.
- Fully aligned with the 12-Factor principle.
Limitations:
- Managing a large number of properties becomes cumbersome.
- Containers do not support native dynamic reloading (a "rolling update" is required when environment variables change).
Versioned external files
Another option is to store parameters in configuration files (YAML, JSON, Properties) located outside the service’s main folder, but still accessible at runtime.
For example, in application-prod.yml, we could have:
payment:
provider: "Stripe"
api-key: "sk_live_XYZ123"
catalog:
url: "http://catalog-service:8080"
These files can be mounted as a volume in Docker containers, downloaded at deployment time from an independent Git repository (GitOps), and integrated with frameworks (Spring Boot allows importing additional files with spring.config.additional-location).
Advantages:
- Easy to use and read, with support for merging and Spring profiles (e.g., application-dev.yml, application-prod.yml).
- Simple versioning in Git, allowing rollback if something goes wrong.
Disadvantages:
- Requires a manual or automated process to distribute these files to each node.
- Handling secrets isn’t always straightforward (you must encrypt them or restrict access).
Centralized Configuration Services
For large microservice ecosystems, a configuration server becomes a key component. Some popular tools include:
- Spring Cloud Config:
- Acts as a bridge between microservices and a Git repository (or other backends).
- The microservice starts up and contacts the Config Server, which provides the appropriate properties based on its application name and profile (application-name, dev/prod, etc.).
- Supports dynamic reloading (if you use Spring Cloud’s Bus and Actuator) and full Git versioning.
- HashiCorp Vault:
- Focused on secret management (keys, passwords, tokens).
- Provides data encryption, access control policies (ACL), and in some cases, dynamic credential generation (e.g., temporary DB credentials).
- Integrates with Java apps, Kubernetes, and more.
- Consul:
- In addition to key/value configuration storage, provides service discovery.
- Can be paired with Vault for encrypted value storage.
Advantages:
- Centralization and scalability: microservices don’t need to "know" where their config is, just the config service endpoint.
- Auditing and traceability: changes are logged and role-controlled.
- Dynamic updates (hot reload) without redeployments (especially with Spring Cloud Config).
Disadvantages:
- Adds complexity and requires maintaining the config server.
- Must have a high availability plan to avoid creating a single point of failure.
3 Detailed example in an eCommerce with Spring Boot and Kubernetes
Imagine our eCommerce platform is made up of four microservices:
- catalog-service: exposes the product catalog (name, stock, price).
- orders-service: manages orders, calculates totals, and coordinates processing.
- payment-service: integrates with payment gateways (Stripe, PayPal).
- shipping-service: calculates shipping costs and manages logistics.
- Config Server:
- It’s a Spring Boot application that includes the spring-cloud-config-server dependency.
- In its application.yml, we define the location of the Git repository containing configurations:
server:
port: 8888
spring:
cloud:
config:
server:
git:
uri: https://github.com/myorg/config-repo
default-label: main
- We activate the server with the annotation @EnableConfigServer.
- Git repository “config-repo”:
- Contains files like catalog-service.yml, orders-service.yml, etc.
- For different environments, we could have catalog-service-dev.yml and catalog-service-prod.yml.
- Let's suppose the content of catalog-service-prod.yml is:
catalog:
db:
url: "jdbc:postgresql://prod-db-host/catalog"
user: "catalog_user"
pass: "SuperSecretPass"
cache-ttl: 300
- catalog-service (Spring Boot microservice)
- In its bootstrap.yml (which loads before application.yml), we specify:
spring:
application:
name: catalog-service
cloud:
config:
uri: http://config-server:8888
profile: prod
label: main
- On startup, catalog-service will make a GET request to /catalog-service-prod.yml from the Config Server, retrieving the properties defined in Git.
- Deployment on Kubernetes:
- We define a Deployment for catalog-service:
apiVersion: apps/v1
kind: Deployment
metadata:
name: catalog-service
spec:
replicas: 2
selector:
matchLabels:
app: catalog-service
template:
metadata:
labels:
app: catalog-service
spec:
containers:
- name: catalog-service
image: myrepo/catalog-service:latest
env:
- name: SPRING_PROFILES_ACTIVE
value: "prod"
- name: SPRING_CLOUD_CONFIG_URI
value: "http://config-server:8888"
- With this setup, each
catalog-servicepod will know how to connect to the Config Server, receiving the updated configuration from catalog-service-prod.yml.
- Configuration change:
- If we want to increase the cache TTL to 600 in production, we edit catalog-service-prod.yml in Git and commit the change.
- We can notify the service to reload the configuration using curl -X POST http://catalog-service:8080/actuator/refresh (assuming we're using Spring Cloud Bus or an Actuator endpoint).
- Without recompiling or redeploying, catalog-service adopts the new value catalog.cache-ttl=600.
This workflow is repeated for orders-service, payment-service, and so on, maintaining configuration in a central and version-controlled location. As the platform grows, this practice becomes essential for governance and security.
Benefits of Externalized Configuration
- Lower risk of leaks: by not storing secrets in code repositories, the chances of exposing sensitive data are greatly reduced.
- Multi-environment deployments: a single binary of orders-service can run in dev, test, or prod without additional recompilation.
- Change traceability: with Git repositories or config services, there is always a history of who changed what and when.
- Hot reload and scalability: especially with Spring Cloud Config, it's possible to update the config on the fly and scale pods without each having a different set of properties.
General Best Practices
- Adopt a "Secure by Design" approach. For externalized configuration, especially protect sensitive data using Vault, Kubernetes Secrets, or strong encryption.
- Version your APIs. CDCT doesn’t eliminate the need to version endpoints when introducing breaking changes. For example, maintain /v1/pay and /v2/pay in payment-service, allowing consumers to migrate gradually.
- Maintain team communication. CDCT's success relies on collaboration; it’s not a substitute for communication but a catalyst to discuss contracts objectively.
- Automate the pipeline. Config collection and contract verification should run in every build process, not just before a release.
Conclusions and Next Steps
Microservices architectures provide scalability and flexibility, but require solid management and validation practices to maintain consistency in a distributed environment. To build a more effective solution to common challenges, we suggest:
- Separate parameters and secrets from code, improving security, control, and ease of updates.
- From environment variables to centralized services like Spring Cloud Config or HashiCorp Vault, the key is to choose the solution that best fits the size and needs of your organization.
- If you're managing a few microservices and only need one or two credentials, start with environment variables or YAML files. As the platform scales, consider adopting a Config Server or Vault.
- Combine with other practices: a robust microservice also needs good log design, distributed tracing (observability), and resilience mechanisms (circuit breakers, timeouts). Externalized Configuration is not isolated—it complements your global DevOps/Cloud Native strategy.
- With externalized configuration, we ensure that each microservice consumes only the parameters it needs in a secure and manageable way, regardless of the environment.
In the next post, we'll explore Consumer-Driven Contract Testing (CDCT). If you have any comments, we’d love to hear from you 👇.
Comments are moderated and will only be visible if they add to the discussion in a constructive way. If you disagree with a point, please, be polite.








Tell us what you think.