This week, an outage at Amazon Web Services (AWS) took down giants such as Duolingo, Fortnite, Slack, Peloton, and PlayStation Network, affecting millions of users and exposing a critical vulnerability in internet infrastructure that made the digital world wobble.
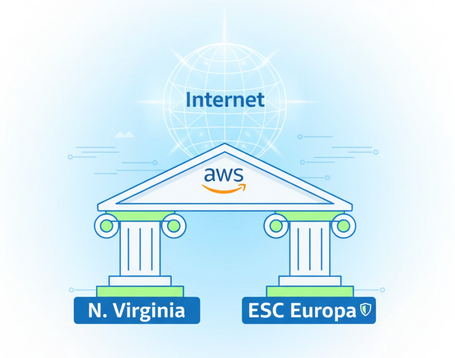
The origin of the chaos, once again, was a single point of failure (SPOF) located in the Northern Virginia region (us‑east‑1). This region is not just any region; it is the brain where centralized, global services are managed such as authentication (IAM), billing, and DNS for a large part of the AWS ecosystem. When Northern Virginia fails, the domino effect is global.
Europe Has the Solution and We Must Use It
For years, architecture professionals and business leaders across Europe have insisted on the need for a sovereign and independent cloud, even if operated by a U.S.‑based company like AWS. This demand is not a protectionist whim, but a strategic necessity for resilience and autonomy.
So far, AWS has given us the option to control where our data and processing are located in European regions. However, the fine print is crucial: metadata (information about information, such as authentication, authorization, and billing data) is still replicated and managed in the U.S. central servers. This creates that critical dependency on the Northern Virginia region.
This is where the forthcoming AWS European Sovereign Cloud (ESC) changes the game. Its main advantage isn’t just that data resides in this or that region (which is essential in itself), but that it provides full independence of the control plane and metadata.
In short, avoiding that SPOF by using its own IAM, billing, and DNS system, completely isolated and operated within the EU by EU‐resident personnel. The ESC is designed to be immune to an operational failure in Northern Virginia, meaning the chain of dependency that caused this week’s outage is broken.
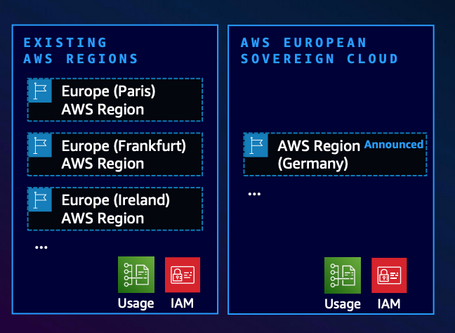
Planning and Next Steps for the European Sovereign Cloud
The rollout of the “European Sovereign Cloud” (ESC) is not a one-off event, but a strategic long‑term programme, structured in clearly defined phases:
- Initial launch. The first operational region will be established in Brandenburg, Germany, with a planned inauguration by the end of 2025. This founding region will mark the beginning of Europe’s sovereign cloud infrastructure.
- Long‑term investment commitment. AWS has committed €7.8 billion through 2040, guaranteeing not only the initial deployment, but also ongoing maintenance, technological evolution and support for the next fifteen years.
- Progressive expansion of service catalogue. From day one the launch will include a full portfolio of core services—compute, databases, AI/ML, and more. The service catalogue will expand continually and respond to the European market’s needs. As a key example of this planned evolution, AWS IAM Identity Center is scheduled to be available in Q1 2026.
- European governance framework. The operation of the ESC will rest on a newly established German‑legal entity created specifically to guarantee digital sovereignty. This entity will maintain an independent advisory board and be managed exclusively by EU citizen personnel, thus ensuring full European control and oversight of the infrastructure.
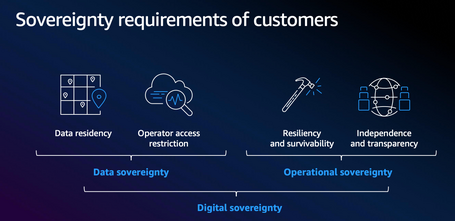
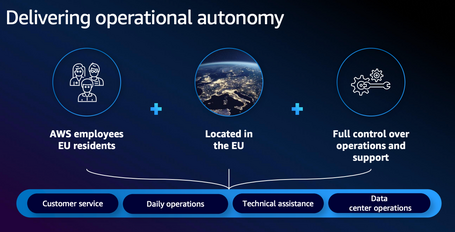
Warning: “Sovereignty” as a Commercial Term
Despite the robust technical safeguards implemented and the strong commercial message AWS projects with its “European Sovereign Cloud”, it is essential not to lose sight of the underlying legal reality.
Regardless of the European‑based architecture deployed, AWS remains a U.S.‑based corporate entity, which keeps it subject to U.S. federal laws. This circumstance has direct and significant implications for any organization storing sensitive data on the platform.
Among these U.S. laws, the US CLOUD Act (Clarifying Lawful Overseas Use of Data Act) stands out—law that grants U.S. federal authorities the ability to demand access to data stored by U.S. companies, regardless of where the data is physically located.
This means that, in theory, even data hosted in German servers under the ESC’s operational control could be subject to U.S. court orders. This legal reality represents a fundamental tension between promised technical sovereignty and the true legal autonomy many European organizations seek.
This point has sparked intense debate among legal experts and digital privacy advocates. The central argument is clear: technical sovereignty, no matter how advanced, does not equate to full legal sovereignty while AWS remains under U.S. jurisdiction. For organizations managing critical workloads (government data, strategic infrastructure or classified information), this limitation represents a real risk that must be carefully evaluated before migrating to the platform.
European Regulatory Framework: DORA and NIS2
The European Union has established an unprecedented regulatory framework to strengthen digital resilience and cybersecurity among its member states via two key regulations.
On one hand, the DORA regulation (Digital Operational Resilience Act), which came into force in January 2023 and is mandatory from January 2025, sets comprehensive digital operational resilience requirements for financial entities. It requires banks, insurers, investment firms and other actors in the financial sector to implement robust technology risk management frameworks, conduct resilience tests and ensure operational continuity in the face of cyber incidents.
On the other hand, the NIS2 Directive (Network and Information Security Directive), approved in December 2022 and which member states had to transpose into national legislation by October 2024, significantly expands the scope of its predecessor (NIS1), introducing strict cybersecurity requirements for critical and essential sectors. NIS2 covers industries from energy and healthcare to digital service providers and critical product manufacturers, forcing them to deploy appropriate technical and organisational measures, report major incidents within defined timeframes and establish clear chains of accountability, including senior management.
Both regulations share a common objective: to ensure that European organisations—especially those managing critical services or sensitive data—maintain minimum levels of security and operational resilience, thus reducing exposure to cyber threats and strengthening Europe’s strategic digital autonomy.
Migrating to the ESC is not strictly required for a bank to continue operating on AWS, but it offers many advantages and may be necessary to fully ensure compliance.
For example: DORA (Chapter II, RTS Article 12) requires financial entities to implement logging procedures that protect the availability, authenticity, integrity and confidentiality of data. These procedures must include measures to secure logging systems and information against manipulation and unauthorized access.
The ESC simplifies this compliance by providing an independent IAM service fully resident within the EU. This ensures that critical operational telemetry—such as CloudTrail logs (roles, configurations and resource access)—is generated and remains natively within its governance domain in Germany.
The non‑ESC alternative involves generating operational metadata in the global commercial partition in Northern Virginia, then implementing and documenting complex secure copying processes to a European region. This “telemetry handling” must be rigorously evaluated, as log forwarding may violate DORA’s sovereignty requirements.
Conclusion: The Road to a More Stable Global Internet
In theory, a company could have weathered the type of outage we suffered this week by distributing its services between AWS’s current central infrastructure and the future European Sovereign Cloud. This dual‑partition architecture is not just a compliance strategy but a powerful business continuity tool.
This could lead to a more stable global internet, where critical services for the economy (banking, logistics, etc.) and for society (Netflix, communication services) are not dependent on the health of a single nerve center.
The strategic implication is even greater: we could see non‑European firms using AWS’s sovereign data centres in Europe as their contingency plan. This could accelerate the proliferation of European data centres and capabilities, turning Europe into the “second leg” on which the global infrastructure of a market‑dominating giant (who already holds 30% of the global cloud market) stands. A key step towards autonomy and, above all, stability.
For any company running critical workloads—such as in banking or insurance—incorporating this new pillar of resilience into their cloud strategy by early 2026 is the most efficient path to ensuring business continuity and meeting regulatory requirements such as DORA or NIS2.
At Paradigma we are following this development closely and will continue analysing the new scenario created by AWS European sovereignty. We look forward to your comments! 👇
Comments are moderated and will only be visible if they add to the discussion in a constructive way. If you disagree with a point, please, be polite.








Tell us what you think.