Do you know what a CASB is and what it is for? And an IGA? Well, in the current situation, where cloud services are changing from a necessity to an obligation, you are going to start hearing about them everywhere. In today’s post, we are going to see what each of these tools consists of.
An IGA (Identity Governance and Administration) facilitates centralised user identity and access control management. It helps to attain the security level and regulation compliance that companies need.
According to Gartner's definition, the basic features that every IGA must have are:
- Management of the lifecycle of identities: information about identities, accounts and permissions is easily managed and maintained by means of access control based on roles.
- Access requests: ability to grant access by automatically managing requests.
- Orchestration workflow: develop specific company workflows with integrated and personalised options.
- Access certification: automate access certification to improve auditing and performance, and reduce the cost of compliance.
- Automatic provisioning: to increase productivity and satisfaction, and reduce the time dedicated to user management.
- Analyses and reports: ability to generate entity audit reports on demand.
- Policy, role and audit management: ability to proactively define and reinforce user access policies across the organisation.
- Management of passwords: to reduce the help-desk load and improve user productivity.
Its functionality often overlaps with that of an IAM (Identity & Access Management). The main difference is that in addition to allowing IAM policies to be defined, reinforced and audited, it also helps to meet the compliance requirements set by some regulations (such as HIPAA, SOX, etc.).
The IAM that comes standard with AWS or Google Cloud Platform will meet all your company’s needs in a pure public cloud model. But if you would like to work on multicloud (with multiple public cloud services) or you must cover a hybrid cloud, it may be necessary to the complement the multiple IAMs with AMIs or SaaS such as CA Technologies or Saviynt, or other products such as SailPoint, Courion, RSA Secure Id, Micro Focus (NetIQ), Omada.
A CASB, or ‘cloud access security broker’, is a cloud security tool that is usually situated between the on-premises infrastructure available to an organisation and the infrastructure that it has in its public cloud. It allows the organisation to apply its security policies beyond its own infrastructure, acting as a gatekeeper.
It also offers visibility over users, data and cloud services by integrating security information and event management solutions. It keeps data safe by means of configurable encryption policies, data loss prevention functionality and tools to achieve file and content trackability.
It prevents major security threats with its ability to identify access from suspicious locations or devices. It also includes detection of users that bypass the IAM or access from compromised accounts and outdated operating systems.
In essence, it can pick up and avoid malicious and anomalous activity. Furthermore, a CASB must allow compliance reports to be generated. In this way, organisations will know whether they satisfy the compliance requirements by specifying who, what, when, where and why.
They offer value because of their ability to give us an overview of which cloud applications are being used across different platforms and the ability to identify unauthorised users. Nowadays, this is very important to guarantee compliance with data protection regulations, especially in those industries where their application must be stricter.
[caption id="" align="aligncenter" width="823"]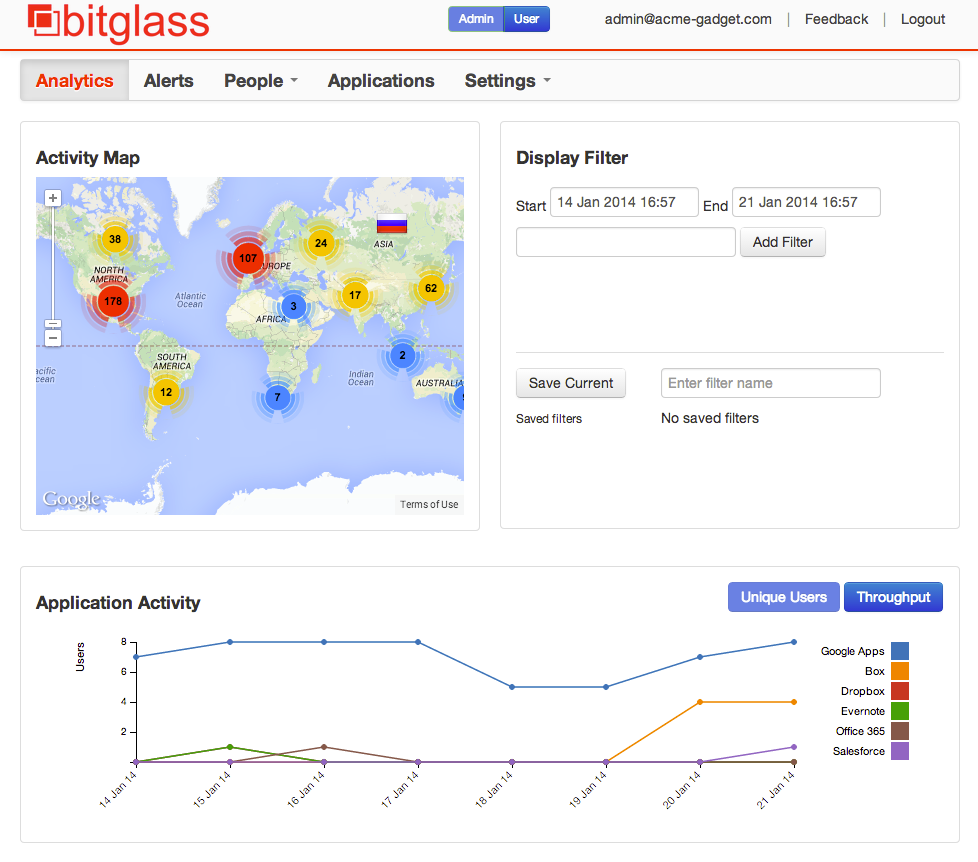
Dashboard of a CASB to display the activity of the different services[/caption]
Different predictions indicate that it will be a security platform required by companies that use cloud services and they predict very high growth in usage over the coming years, going from 5% in 2015 to 85% in 2020.
The companies that are currently using these tools are considered to have the clearest vision of the future and the best security strategies. Even if it is only because its use implies that a minimum set of security policies has been defined and it is clear who should be using what and why.
Even though it is an emerging tool, we can currently find a host of products on the market. Some of the best and most well-known are: BitGlass (even available on AWS’s marketplace), SkyHigh, Ciphercloud, NetSkope or Microsoft Cloud App Security (previously Adallom).
There are some that are exceptional in the layout and analysis of information. Some include extreme encryption and offer high flexibility. Others are very good for application control or compliance with international data protection regulations.
The prices usually go from $2 per user per month up to about $30, depending on the number of services included in the subscription. The simplest bundles begin by charging for log discovery and analysis features, and the final bill grows as features are added, such as: encryption, DLP, malware protection for mobile devices, or for specific applications.
Now that we understand everything that they can offer us, we should not lose sight of them, as they will be one of the tools that will help us to complement the security of our cloud environments.
They will be an extra help to ensure that everything is perfectly laid out and controlled when we migrate our systems or develop new projects in a hybrid cloud or multicloud. And they will allow us to manage users and access policies on different systems and tools without it being a burden for our business to grow globally.
Comments are moderated and will only be visible if they add to the discussion in a constructive way. If you disagree with a point, please, be polite.





Tell us what you think.